Medical imaging offers windows into health trajectories, but digital data transmission risks exposure.
As records become irresistible hacker targets, providers balancing accessibility with privacy protections enter slippery territory. Yet patient trust and regulatory non-compliance inflict high costs when security fails.
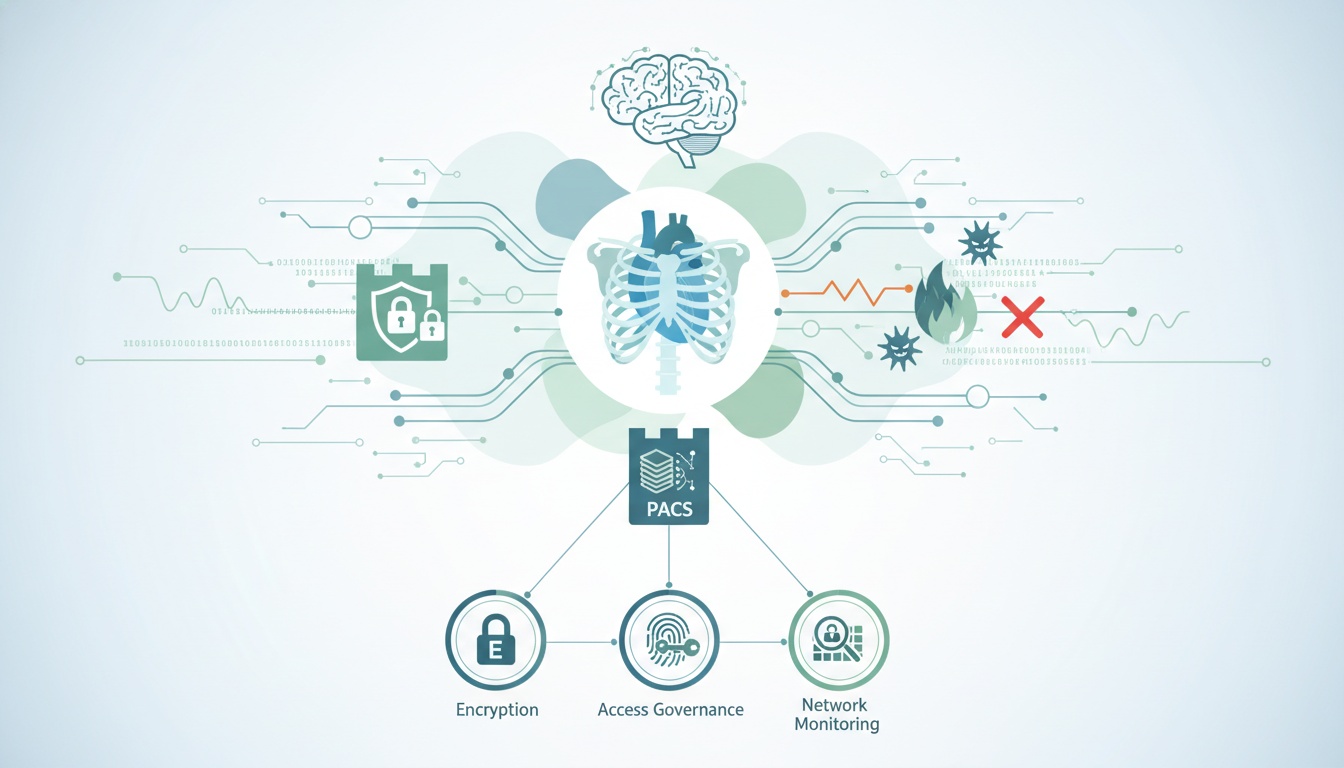
Cyber defenses demand strategic strengthening for North American healthcare organizations leveraging Picture Archiving and Communications Systems (PACS) to condense diagnostic storage and transfer.
We dive into confidentiality beaches’ repercussions and system vulnerabilities permitting them. Learn how encryption, access governance, and network monitoring comprise a robust, integrated security framework protecting institutional reputations and patient well-being.
By illuminating technical and human oversight principles for care facilities and PACS providers alike, our insights aim to educate and empower. Because when data flows freely, barriers to care drop - but not at the expense of safety. Join us in exploring peace of mind protocols.
Radiological data is critical in healthcare due to its detailed insights into a patient's health status. This sensitive and voluminous data often comprises various imaging types, such as X-rays, MRIs, and CT scans.
It contains highly confidential personal health information (PHI) that requires stringent protection under regulations like HIPAA.
The sensitivity of this data stems from its comprehensive nature. It often reveals intricate details about a patient's medical history, current health condition, and potential future health risks.
The consequences of a data breach in radiology can be severe and multifaceted. For patients, it could mean the unauthorized disclosure of their private health information, leading to privacy violations and potential data misuse.
For medical businesses, a breach can result in significant legal repercussions, loss of patient trust, and substantial financial penalties. The reputational damage from such incidents can have long-lasting effects on a healthcare provider's standing in the industry.
Cybersecurity in healthcare, particularly radiology, has recently gained paramount importance. Potential cyber threats have escalated as healthcare providers increasingly adopt digital technologies for storing and transmitting diagnostic data.
Due to the high value of medical data, the healthcare sector has become a prime target for cybercriminals. This shift necessitates a robust cybersecurity framework to protect sensitive patient information from unauthorized access and breaches.
Medical data storage and transmission systems face a variety of cyber threats. These include ransomware attacks, where malicious software encrypts data, rendering it inaccessible until a ransom is paid. Phishing attacks are common, where attackers trick healthcare staff into revealing sensitive information or credentials.
Additionally, there are threats of insider breaches, either intentional or accidental, due to inadequate security protocols or employee negligence. Other threats include Distributed Denial of Service (DDoS) attacks, which can disrupt the availability of critical medical services, and malware infections that can compromise the integrity of medical data.
Picture Archiving and Communication Systems (PACS) have become integral in modern healthcare, particularly in managing and storing diagnostic imaging data.
PACS streamlines the storage, retrieval, and sharing of medical images, such as X-rays, CT scans, and MRI images.
This system efficiently accesses patient imaging records, facilitating timely diagnosis and treatment. In essence, PACS is the backbone of digital imaging in healthcare, replacing the traditional methods of handling physical films.
Despite the efficiency and advancements brought by PACS, they are not immune to cybersecurity threats.
One of the primary vulnerabilities lies in their connectivity. PACS are often connected to various networks and devices within a healthcare facility, making them susceptible to network-based attacks. If not properly secured, unauthorized individuals can potentially access sensitive patient data.
Another vulnerability is the software component of PACS. Like any software, PACS can have security flaws or bugs that hackers can exploit. These vulnerabilities can be particularly problematic if the system is not regularly updated with security patches.
The user interface of PACS also presents a potential risk. User error or lack of adequate training can lead to accidental breaches, such as unintentionally sharing sensitive data.
There have been notable incidents where the security of PACS was compromised. For instance, some healthcare institutions have experienced data breaches where patients' personal health information was accessed illegally due to insufficient security measures in their PACS.
These incidents often resulted from unpatched software vulnerabilities or inadequate network security.
Several lessons have been learned from these breaches. Firstly, the importance of regular software updates and patch management cannot be overstated. Keeping the PACS software up-to-date is crucial in protecting against known vulnerabilities.
Secondly, network security measures such as firewalls, intrusion detection systems, and network segmentation are essential in safeguarding PACS from unauthorized access.
Lastly, the human element plays a significant role in the security of PACS. Regular training and awareness programs for PACS staff are vital in minimizing the risk of accidental breaches and ensuring everyone understands the importance of data security.
PostDICOM, as a provider of PACS solutions, recognizes the criticality of cybersecurity in the healthcare sector. Their PACS systems are designed for efficiency and ease of use but with a strong emphasis on security.
These systems are equipped with multiple layers of protection to safeguard sensitive patient data against cyber threats.
PostDICOM takes a comprehensive approach to addressing common cybersecurity challenges in PACS. Understanding that threats can come from various sources, their strategy encompasses technical and human-centric solutions.
They ensure their PACS are fortified against network-based attacks, software vulnerabilities, and potential user errors.
One key aspect of PostDICOM’s approach is the continuous monitoring and updating of its systems. They recognize that cybersecurity is an ongoing battle, with new threats constantly emerging.
Therefore, their PACS solutions are regularly updated with the latest security patches and upgrades to combat emerging vulnerabilities.
PostDICOM implements several robust security protocols and measures to protect patient data. Firstly, their PACS solutions use advanced encryption technologies.
This encryption is applied to data at rest and in transit, ensuring that patient information is always protected, whether stored or shared.
Network security is another critical area of focus. PostDICOM’s PACS is designed to operate within a secure network environment, with firewalls and intrusion detection systems to prevent unauthorized access.
They also employ network segmentation strategies, ensuring that the PACS network is isolated from other parts of the healthcare facility’s network, thereby reducing the risk of cross-system breaches.
In addition to these technical measures, PostDICOM strongly emphasizes user access controls. Their systems are configured to ensure that only authorized personnel have access to sensitive data, and they employ rigorous authentication methods to verify user identities. This approach minimizes the risk of accidental breaches or unauthorized access.
Furthermore, PostDICOM recognizes the importance of user training and awareness. They provide comprehensive training to healthcare staff on the proper use of their PACS and on general cybersecurity best practices.
This training ensures that users are aware of potential security risks and know how to avoid them.
 - Created by PostDICOM.jpg)
In the ever-evolving cybersecurity landscape, staying ahead of threats is crucial, especially for systems like PACS that handle sensitive medical data.
Advanced security technologies are not just add-ons but essential components of a robust PACS solution. These technologies ensure that patient data is protected from increasingly sophisticated cyber threats.
Encryption stands at the forefront of safeguarding data in PACS. It serves as the first line of defense, ensuring that patient data, whether at rest or in transit, is unreadable to unauthorized individuals.
Encryption transforms sensitive data into a coded format, which can only be decoded with the correct key. This process is vital in preventing data breaches, as even if the data is intercepted or accessed by unauthorized parties, it remains secure and unintelligible.
Another critical aspect of PACS security is secure access controls. These controls ensure that only authorized personnel can access sensitive patient data. This is particularly important in healthcare settings where multiple users interact with the PACS.
Secure access controls involve robust authentication processes, often including multi-factor authentication (MFA), which requires users to provide two or more verification factors to gain access. This method significantly reduces the risk of unauthorized access due to stolen or weak passwords.
Network security is also a key component of protecting PACS. This involves safeguarding the network infrastructure that supports PACS from various cyber threats.
This security framework includes firewalls, intrusion detection and prevention systems, and regular network monitoring. These measures help detect and prevent unauthorized access and identify any unusual activity that could indicate a security breach.
PostDICOM integrates these advanced security technologies into their PACS solutions to provide a comprehensive security framework. They employ state-of-the-art encryption to protect data, ensuring that all patient information stored or transmitted through their PACS is secure.
PostDICOM implements stringent authentication mechanisms, including MFA, regarding access controls to ensure that only authorized users can access the system.
Furthermore, PostDICOM’s PACS solutions are designed with network security in mind. They incorporate robust firewalls and advanced intrusion detection systems to monitor and protect the network infrastructure. Regular security audits and updates ensure that the network defenses remain strong against new and evolving cyber threats.
For medical businesses in North America, the security of PACS is not just about the technology itself but also about how it is managed and used within the organization. Implementing best practices is crucial to enhance the overall security of PACS and protect sensitive patient data.
One key area where medical businesses can strengthen their PACS security is through staff training and awareness. Employees should be educated about the importance of data security and their specific roles in maintaining it.
Training programs should cover topics like secure login practices, recognizing phishing attempts, and adequately handling patient data. Regular refresher courses are essential to update staff on new threats and security protocols
Another vital practice is conducting regular security assessments. These assessments should evaluate all aspects of the PACS, from the software and hardware components to the network infrastructure and user access controls.
The goal is to identify and address potential vulnerabilities before they can be exploited. These assessments can be conducted internally, but it’s also beneficial to occasionally bring in external experts for an unbiased review.
Keeping the PACS software and associated systems up to date is crucial. Software updates often include patches for security vulnerabilities identified since the last update. Delaying these updates can leave the system exposed to known risks.
Therefore, medical businesses should have a process for timely system updates and patch management.
Collaborating with PACS providers like POSTDIcom can significantly enhance security. POSTDIcom can offer expert guidance on configuring the PACS for optimal security based on the medical business's specific needs and challenges. They can also provide support for regular system updates and maintenance.
Moreover, POSTDIcom can assist in setting up advanced security features like encryption, network security measures, and secure access controls. They can also offer training resources or assist in developing customized training programs for staff.
Ultimately, fortifying PACS comes down to vigilance across vectors, from software to staff habits. By instilling security-conscious cultures reinforced through training, the human firewall thickens.
Regularly assess systems for weaknesses at both technical and policy levels before criminals probe first. Leverage providers’ offerings like encryption and activity monitoring to create multilayered defenses.
While postures must flex with new threats, stewarding health data is fundamentally an enduring covenant of trust between patients and caregiver institutions. Demonstrate commitment by collaborating cross-functionally, investing adequately in prevention, and responding transparently to any breach.
Though eliminating risk remains impossible, its radical reduction uplifts care standards industry-wide.
We all have roles upholding patient privacy - our insights illuminate the following right action. Ultimately, PACS cybersecurity fuels the confidential exchange of life-saving imaging unconstrained by fear. And that revelation powers the brightest possible futures.
|
Cloud PACS and Online DICOM ViewerUpload DICOM images and clinical documents to PostDICOM servers. Store, view, collaborate, and share your medical imaging files. |